Connect-AzAccount (Not required if you are using cloudshell)
If your account is associated more than one subscription, identify and set the active subscription
$context = Get-AzSubscription -SubscriptionId <subscription-id>
Set-AzContext $context
Register the AllowNFSV3 feature by using the following command.
Register-AzProviderFeature -FeatureName AllowNFSV3 -ProviderNamespace Microsoft.Storage
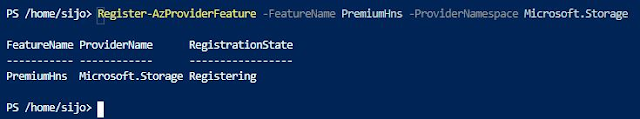
Register the PremiumHns feature by using the following command as well.
Register-AzProviderFeature -FeatureName PremiumHns -ProviderNamespace Microsoft.Storage
HNS - The hierarchical namespace allows you to define ACL and POSIX permissions on directories, subdirectories or individual files. You can also use role-based authentication and Azure Active Directory (Azure AD) to support resource management and data operations
Register the resource provider by using the following command.
Register-AzResourceProvider -ProviderNamespace Microsoft.Storage
It will take around 1 hour to complete registration process, you can run below commands to verify the status of registration.
Get-AzProviderFeature -ProviderNamespace Microsoft.Storage -FeatureName AllowNFSV3
Get-AzProviderFeature -ProviderNamespace Microsoft.Storage -FeatureName PremiumHns
2.Create a storage account
Supported region : US East, US Central, US West Central, Australia Southeast, North Europe, UK West, Korea Central, Korea South, and Canada Central
NFS 3.0 supported only in below account kind; General purpose v1,v2 and blobstorage are not supported at the moment.
Performance tier : Premium
Account kind : Block blob storage
Virtual Network and Security requirements
At the moment in-order to secure data account key authorization, Azure Active Directory (AD) security, and access control lists (ACLs) are not yet supported in accounts that have the NFS 3.0 protocol support enabled on them.
So only way to support this kind of storage account is by placing them into a subnet in a VNET and enable restrictions with the help of NSG, virtual machines from same VNET/subnet can access the blob containers created in the storage account.
Also you can enable VNET peering with other VNETS to get the blob containers accessed from other networks in azure, blob containers can be mounted to the machines in on-prem infrastructure in case if you have VPN/Express route connection via virtual network gateway into the VNET where storage account is contained.
Note: NFS 3.0 feature cannot be enabled unless the storage account is placed into a VNET and subnet.
On advanced tab you must enable the HNS and NFS 3.0. If it is greyed out check the NFS 3.0 registration status and ensure that the storage account is placed into a VNET/Subnet.
Verify the below before submitting the settings for storage account creation, once it is deployed the account kind and related configurations cannot be reverted.
3. Create Blob container
Once the storage account is successfully provisioned, navigate to Data Lake storage --> select containers and click on +container to create a blob container
Ensure that the access level is set to private anonymous
4. Setup NFS 3.0 client on windows machines
In-order to mount a blob container into windows machine using NFS 3.0 you must install NFS 3.0 client into the windows machines.
Windows Servers
Open server manager --> Add roles and features --> select "Client for NFS" from feature tab and complete the installation and reboot the machine.
Windows 10 workstations
Open control panel --> add or remove programs --> Turn Windows features on or off --> select "client for NFS" check box from under the "Service for NFS" --> complete the installation and reboot the machine.
5. Mount the blob container
The blob container can be mounted into the server(W2K16)/workstation(windows 10) by entering below command from a administrative command prompt.
mount -o nolock <storage-account-name>.blob.core.windows.net:/<storage-account-name>/<container-name> *
Storage-account-name - replace with your storage account name
Container-name - replace with your container name
6. Write permission issue with mounted container
At this stage the mounted container blob will not have write permission, lets check it by creating a new file into it.
If you need write permissions, you may need to change the default UID and GID that Windows uses to connect to the share. To do this, run the following PowerShell commands as an administrator from the windows machine:
New-ItemProperty -Path HKLM:\SOFTWARE\Microsoft\ClientForNFS\CurrentVersion\Default -Name AnonymousUid -PropertyType DWord -Value 0
New-ItemProperty -Path HKLM:\SOFTWARE\Microsoft\ClientForNFS\CurrentVersion\Default -Name AnonymousGid -PropertyType DWord -Value 0
Lets now check the write access into the blob container mounted into a windows machine
Check out whether the file created is showing up in the container blob on Azure portal.
Note: We can expect new features such as Azure AD RBAC, ACL and account key in-order to secure the mounted blob containers also many of the configurations may change once the it is released to general; so always refer Microsoft documentations to get latest updates.
Reference :
Guys kindly check it out and get familiar with the concepts of container blob mounting, the above link to Microsoft documentation will help you understand about mounting of blobs containers into Linux operating systems as well.
Thanks for reading 👍
























Good...
ReplyDeleteWill read fully and update
ReplyDeletebest informartion technology
ReplyDeletebest informartion technology
best informartion technology
best informartion technology
best informartion technology
best informartion technology